
Information Security Governance Risk & Compliance Services
Our ISO 27001 implementation services are designed to help organizations effectively implement and achieve compliance with the ISO 27001 standard, which focuses on information security management systems. We offer comprehensive support throughout the entire implementation process, ensuring that our clients establish a robust framework to protect their valuable information assets.
Chat with an expert
We’ll reach out to answer all your questions
Achieving accredited ISO 27001 certification demonstrates that your organization follows information security best practices, and has successfully implemented an Information Security Management System, audited by an independent expert assessment.
Enhance reputation, business efficiency, customer satisfaction with our ISO 27001 certification.
ISO 27001 is an internationally recognized standard
Promotes a risk-based methodology
Allows organizations to better manage information security
Implements an Information Security Management System (ISMS)
Systemic approach to implementing, operating, and maintaining compliance


ISO27001 Compliance

Our PCI DSS implementation services are designed to assist organizations in achieving compliance with the Payment Card Industry Data Security Standard (PCI DSS). This standard is essential for businesses that process, transmit, or store payment card information. We offer comprehensive end to end support throughout the implementation process to ensure that your organization meets all the necessary requirements.
PCI DSS Compliance
Customized solutions, expert reviews and analysis to support streamlined, cost-effective compliance.
We help your organization understand which controls are applicable and which systems must be protected. And then we help uncover any security and compliance shortcomings.
PCI DSS compliance project plans
scope validation
Self-assessment questionnaires
Attestation of compliance




Top-down Approach






Risk Based Approach
Process Based Approach
Best practice Aligned

Customized solutions, expert reviews and analysis to support streamlined, cost-effective compliance.
Our SOC 2 Type II implementation services are designed to assist organizations in achieving compliance with the Service Organization Control (SOC) 2 Type II framework. We help your organization understand which controls are applicable and which systems must be protected within your business context. And then we help uncover any security and compliance shortcomings including;
Compliance project plans
Risk Management
Policy & associated procedures development
Security Performance monitoring & measurement
Certification audit support
SOC 2 Type II defines criteria for managing customer data based on five “trust service principles”—security, availability, processing integrity, confidentiality and privacy. SOC 2 is an auditing procedure that ensures your service providers securely manage your data to protect the interests of your organization and the privacy of its clients. For security-conscious businesses, SOC 2 compliance is a minimal requirement when considering a SaaS provider. As a non prescriptive standard, SOC 2 management systems are unique to each organization. In line with specific business practices, each organization designs its own controls to comply with one or more of the trust principles.


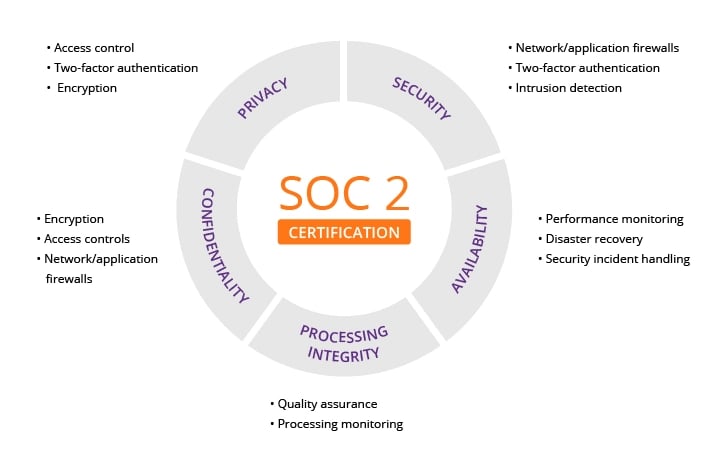
As a non prescriptive standard, SOC II Type II management systems are unique to each organization. In line with specific business practices, each organization designs its own controls to comply with one or more of the trust principles.
SOC II Type II are essential for stakeholders need to gain confidence and trust in a company’s security processes, provide a competitive edge and effective information security risk management.
SOC II Type II Compliance

We adopt a straightforward approach. We adhere to a proven methodology that aligns with the plan-do-check-act principles. Additionally, our management services incorporate competence-building courses, empowering internal teams to effectively oversee the management system long after the consulting services have concluded.



We offer comprehensive cyber security strategy services to help organizations develop robust and proactive approaches to protect their digital assets and mitigate cyber threats. Our services are tailored to address the unique cyber security challenges faced by businesses today.
We offer comprehensive cyber security maturity assessment services to help organizations evaluate and improve their cyber security capabilities. Our assessments provide valuable insights into an organization's current cyber security maturity level, identify areas of strength and improvement, and guide the development of a roadmap for enhancing cyber security practices.


Information Security Strategy Development
Information Security Maturity Assessments



